Launching applications under alternative permissions
Runas /profiles /user:[Admin Identifier] [Command]
z.B.: runas /profiles /user:in\admi2401 cmd.exe
If one starts an application under alternative permissions, then all applications, which are started from it, inherit the permissions of the alternative identifier. I.e. if one starts e.g. the command line (CMD.EXE) under an alternative identification and calls from this command line a further program, like e.g. regedt32.exe o.a., then this application is executed also under the same authorizations, as the source application from which it was started. It should be noted that starting EXPLORER in this way is unfortunately not possible. This problem is also encountered with other programs. The only special thing about Explorer is that it is always started automatically when you log on to the computer interactively, because Explorer manages the desktop environment, and thus an EXPLORER instance is always already present after a successful logon. For this reason, a started EXPLORER will always have the permissions of the locally logged in user. To work around this behavior, an entry must be made in the registry for the user who wants to start EXPLORER under an alternate identifier. To make this change simply start the application regedt32.exe within the command line with the alternative permission and add or change the following value as follows:
HKCU:\Software\Microsoft\Windows\CurrentVersion\Explorer\Advanced
[REG_DWORD] SeparateProcess := 1
From now on, when EXPLORER is started within the command line with alternative permissions, a completely new instance of EXPLORER is always executed, which then also inherits the permission from the command line with the alternative permissions.
Identify the applications running with alternate permissions
Applications that are started under alternative permissions usually have more extensive permissions on the local system or on the entire network. Applications that are started under this identifier therefore deserve special attention. It therefore makes sense to distinguish these applications from other applications by their appearance, so that it is immediately apparent under which identifier the application is running.
Applications that are launched under Windows almost all store their appearance (font, font size, window color, window size, etc.) in the registry. In order to make these applications recognizable when working under privileged rights, some settings must be made in the registry.
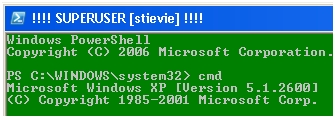
Command Line
With the following registry settings all command line calls are started with the following appearance. (Green background, gray font, title on !!!SUPERUSER [LOGIN] !!!.
HKCU\Software\Microsoft\Command Processor
[REG_SZ] AutoRun := "TITLE !!!! SUPERUSER [%username%] !!!!"
HKCU\Console
[REG_DWORD] ScreenColors := 27
Explorer
Explorer can also be made aware of its special tasks via settings in the registry and a small bitmap.
HKCU\Software\Microsoft\Internet Explorer\Toolbar\
[REG_EXPAND_SZ]BackBitMap = "[PFAD_ZUR_BITMAP_DATEI]\Adm32x32.bmp"
Internet Explorer
Up to version 6.0 of Internet Explorer, the background bitmap file of the toolbars, which was already applied to Explorer, was also used in Internet Explorer. Starting from the version 7.0 of the Internet Explorer one has only the possibility to write a Cascading Style Sheet and to apply this Stylesheet for the Internet Explorer. A side effect of this approach is that many of the snap-ins in the Microsoft Management Console are also influenced by this style sheet, because Internet Explorer is used internally in various places there. It seems that it is no longer possible to design the background of the toolbar and that only the pages displayed by IE can be identified by a stylesheet. But the structure of the stylesheet is kept very simple:
---ie7adm.css---
* { background-color:red;}
In the registry, the new stylesheet must still be made known to Internet Explorer:
HKCU:\Software\Microsoft\Internet Explorer\Styles
[REG_SZ] User Stylesheet := [PFAD_ZUM_STYLESHEET]\ie7adm.css
Commands on the command line for administrative tasks
System control
(first start the command line, as described above, with administrative permissions, then execute the corresponding command)
| appwiz.cpl | Software |
| desk.cpl | Display |
| firewall.cpl | Windows Firewall |
| intl.cpl | Region and language options |
| main.cpl | Mouse |
| mmsys.cpl | Sounds and audio devices |
| nusrmgr.cpl | User accounts |
| sysdm.cpl | System |
| timedate.cpl | Date and time |
| wscui.cpl | Security Center |
| wuaucpl.cpl | Automatic Updates |
more commands on winfaq.de
Microsoft Management Console
(first start the command line, as described above, with administrative permissions, then execute the corresponding command)
| compmgmt.msc | Computer Administration |
| services.msc | Services |
| eventvwr.msc | Event display |
| diskmgmt.msc | Disk management |
| devmgmt.msc | Device Manager |
| dfrg.msc | Defragmentation |
| fsmgmt.msc | Shared folders |
| lusrmgr.msc | Local users and groups |
| gpedit.msc | Group policies |
| secpol.msc | Local security settings |
| pkmgmt.msc | Public Key Management |
Commands
| Regedt32.exe | Registry Editor |
| Explorer.exe | File explorer |
| %SystemDrive%\Programs\Internet Explorer\iexplore.exe | Internet Explorer |
| mmc.exe | Microsoft Management Console, with file > add Snap-in > Add you can choose a snap-in |
Alternative Netware Login
In order to be able to use the permissions of the alternative identifier in a Novell environment as well, you have to do something more cumbersome. The application that represents the Novell login in an interactive desktop session is the nwtray.exe application. Everyone who works with a Novell client knows the nwtray.exe as the red N (Novell Services) in the lower right corner of the taskbar. The problem is that nwtray.exe runs under the identifier you used to log in to the desktop interactively and thus not under the alternative identifier. You have to close this application and then restart it under the alternative ID. Unfortunately, the application cannot be closed simply by clicking a button. For this reason, nwtray.exe must be closed by terminating the process. The easiest way to do this is by using the command line:
C:\>Taskkill /f /im nwtray.exe
Now it is important to restart nwtray.exe again, making sure of course that it is called from the console with the alternative identifier.
C:\> nwtray.exe
After entering the command, you may see two red Ns at the bottom right of the desktop taskbar. This is usually due to the fact that after closing nwtray.exe somewhat brutally, it has not found time to update its display area. If you move the mouse briefly over both Ns, the N for which no more nwtray.exe is loaded will disappear.
Now one can click with the right mouse button on the still existing N and select the context menu the Novell login, in order to log on under its alternative identification with Novell. After successful logon to Novell, you now have the permissions of the alternative identifier in Novell in the command line from which the nwtray.exe was started. Even if you now start the Explorer from this console, you will receive the alternative Novell permissions in the Explorer and can thus access directories and other objects in the Novell environment with the alternative permissions.
- arbeiten als admin.pdfcomplete description as Pdf document
- cstAdmProf.zipScript + BMP file to make recognizable... (Execute the script after login as admin)
Continue with the »Golden Rules«
| 13 Golden Rules of IT Security | |
|---|---|
| ← Back to rule no. 4: Use secure passwords | → Continue with rule no. 6: Caution with e-mail, messengers and browsers |
