via Sectigo
With an SSL server certificate, your server is certified by a trustworthy authority. This makes it possible for a user to verify the authenticity of the server beyond doubt.
Server certificates can be applied for by the IT staff of the Weimar universities.
1. Read the Certification Policy
For the issuing of certificates by the BU Weimar CA, the Certification Guideline of the DFN-PKI is authoritative (PDF; in German).
2. Generate a key pair and create a certificate request
Create a Certificate Signing Request (CSR) and a private key for your server. The certificate request is then added to the Sectigo request form.
To generate the certificate request and the private key you can use tools of the respective server software or openSSL. The length of the private key should be 4096 bits.
Use these attributes in your certificate request:
- CN=<enter the server name to be certified here>
- O=Bauhaus-Universitaet Weimar
- L=Weimar
- ST=Thueringen
- C=DE
An e-mail address must not be included.
3. Request the Certificate via Sectigo
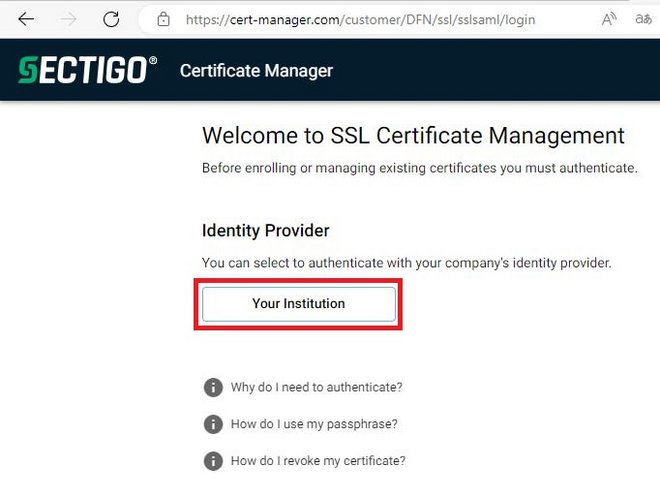
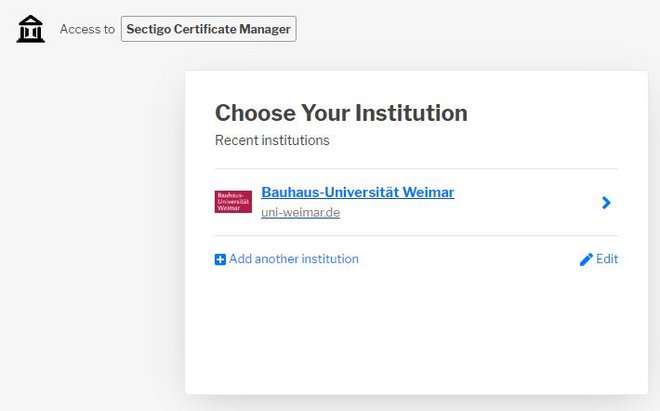
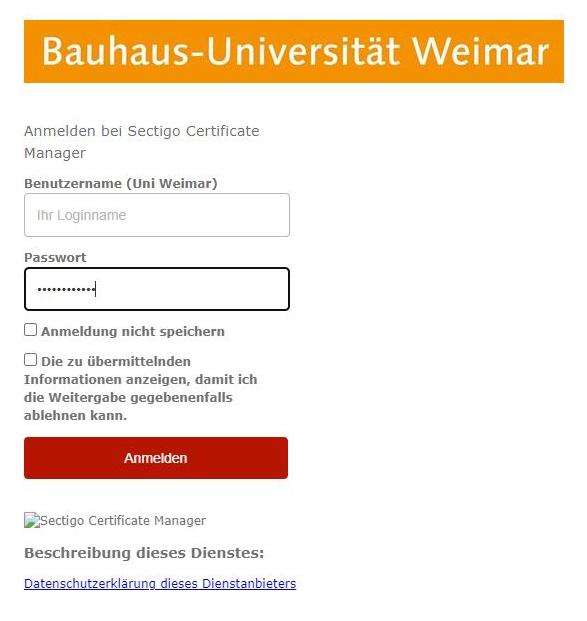
Access the Sectigo-Portal auf, click on Your Institution here:
Organization, Department and Email are filled in automatically.
For Certificate Profile, OV Multi-Domain should be selected.
The Certificate Term is limited to 1 year.
Upload the CSR created at the beginning via Upload CSR or paste it directly under CSR*.
The Common Name is taken from the CSR.
If necessary, entries can be made under Subject Alternative Names.
If no entry is made under External Requester, the entry of the email address from Organisation, Department, Email is used. The e-mail address of the person submitting the request should be entered here.
The Comments field is optional.
If you activate the option Auto Renew, the certificate will be renewed automatically with the same parameters as the initial application – you will receive the renewed certificate by e-mail. (The private key will be used further on. If you are not sure whether it has been compromised in the meantime, create a new certificate request).
Under Days before expiration you specify how many days before the certificate expires the renewal process should be started.
Click Submit to finish.
4. Downloading the Certificate
When the requested certificate has been created, you will receive an email from the system.
The e-mail contains the certificate ID that you need to download, renew or revoke the certificate via the portal. Furthermore, the e-mail contains various links for downloading the certificate.
The following options are offered:
Server certificates:
- Certificate only, PEM encoded: contains only the server certificate in PEM format
- Certificate (w/issuer after), PEM encoded: PEM encoded first contains the server certificate, then the issuing CA certificate and then other intermediate CA certificates of the CA chain, but not the root CA certificate, all certificates individually in PEM format – for Apache / nginx)
- Certificate (w/chain), PEM encoded: contains the root CA certificate first, followed by the intermediate CA certificates, the issuing CA certificate of the CA chain and finally the server certificate, all certificates individually in PEM format
- PKCS#7: contains a binary PKCS#7 structure, consisting of the server certificate first, then the issuing CA certificate and then further intermediate CA certificates of the CA chain and at the end the root CA certificate - for Microsoft IIS
- PKCS#7, PEM encoded: contains a PEM-formatted PKCS#7 structure, consisting of the server certificate first, then the issuing CA certificate and then further intermediate CA certificates of the CA chain and at the end the root CA certificate
CA certificates:
- Root/Intermediate(s) only, PEM encoded: contains the CA certificate chain (without the server certificate) from the root CA (first) to the issuing CA of the server certificate, all certificates individually in PEM format
- Intermediate(s)/Root only, PEM encoded: contains the CA certificate chain (without the server certificate) from the issuing CA of the server certificate (first) to the root CA certificate, all certificates separately in PEM format
Select the appropriate format and download the certificate.
5. Import the Certificate to the Server
The certificate can be installed on the server now.
Instructions